Nowadays every body is
worried about having their system or phone compromised. They have a lot of stuff planned. However, in my opinion, if we adhere to and take certain precautions, we will be on the internet safely. You wouldn't be hackable by anyone.There are a lot of persons and organisations who can notify you whether your phone or system will be hacked, at which point hackers will steal some of your personal information and data.
Ladies and gentlemen, please do not be alarmed; we are here to explain how we can identify viruses and malicious software on our phone or computer.
1) What is Malware?
Ans: Any software purposely created to harm a computer, server, client, or computer network is known as malware. The term "malware" refers to any damaging or parasitic software that is specifically designed to do harm to your server, computer, network, or phone. There are several names for it, but they all refer to the same thing. Ransomware is a type of software that literally encrypts your data and demands payment in exchange for access to it. Threats include disclosing secrets or exposing data, and the victim is left with little choice but to pay the "ransom."
Viruses and Other Types Of Malware
Malicious software that can infiltrate your phone is known as malware. Malware includes computer worms, Trojan horses, spyware, ransomware, and other programmes that are intentionally written to do damage.Malware can be used by cybercriminals to gain access to your personal data, and in some situations, they may use that sensitive data to perpetrate fraud or identity theft.
A specific kind of malware that infects a computer or other device and its programmes is called a virus. It's possible for a cybercriminal to install a virus on your device without your knowledge or agreement. Once on your device, these viruses could be able to add new, malicious malware that can track and control your internet behaviour.
2) How do we Know that which software or which application is malicious?
Ans - First of all we will discuss that how we can protect our system or Pc from malicious software, malware, virus and many more thing. The name of the first tool is:
A) Netstat (Network statistics): is a command-line network utility tool that shows statistics for a variety of network interface (network interface controller or software-defined network interface) and network protocol connections, including both incoming and outgoing transmission control protocol connections. It is accessible on operating systems similar to Unix, such as MacOS, Linux, Solaris, and BSD, as well as on Windows NT-based operating systems, such as Windows XP, Windows Vista, Windows 7, Windows 8, and Windows 10.
Click the start button --->Run --> cmd
taskkill /pid (paste the pid of th
This command will show you all working ports and listening ports. If you can see from the second last option my ip address is 192.168.43.150: my listening port is 2640 and my connected ip is 47.89.113.224: and my service is https and status of connections is established.
After finding the connected ip you open your browser and type ip lookup and grab the information of that ip. This work will help you to know which type of ip is used by your system.
Now suppose that we want to know which application is using my network connection, the command is very simple - netstat -b and you will see that you got that application. If you find that application which is used by your network connection and you must use your port number necessary then write this command at application) /F
1) https://www.man7.org/linux/man-pages/man8/netstat.8.html
2) https://docs.oracle.com/cd/E19683-01/806-4075/6jd69oa95/index.html
B) Tcpview: TCPView is a Windows application that displays thorough listings of all TCP and UDP endpoints on your system, together with the local and remote addresses and the current status of TCP connections. The owner of the endpoint's process is likewise listed by TCPView. A more useful and simply organised subset of the Windows-shipped Netstat programme is provided by TCPView.You can download tcpview from here:-
https://docs.microsoft.com/en-us/sysinternals/downloads/tcpview
if you find that particular malicious and malware application in your system then open your browser again and type virus total site. This site will help you to find malicious app in file or application virus total link.
https://www.virustotal.com/gui/home/upload
Now talking for android and mobile phone how do we detect and how can we be secure
1) In Android or IOS we have only four way to detect. First check the application logo and if the logo is blurry and cannot be seen clear then don't install that application in your phone.
2) if the logo is good then check the name and read review of that application.
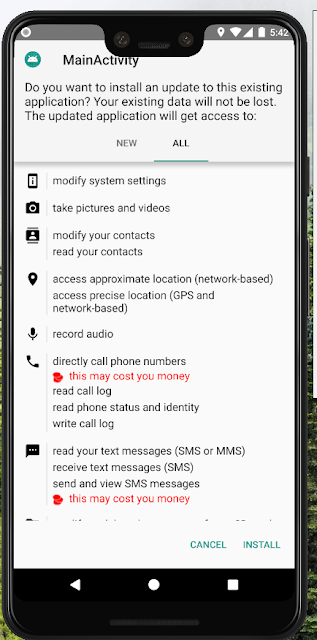
3) if the application looks like this
then don't install because these type of an application is Demanding money from you.
4) after doing these three steps if you still thinks that your phone is hacked then follow this step, it is very important.
Close your data connection and switch the phone into airplane mode after the airplane then check your phone if the phone is still heating, if it is so then your phone has been manipulated or you can call hacked
And some basic tips and tricks is there.
1) Pop-up
The number of pop-up ads in hacked phones suddenly increases in abundance. When you surf internet, it will bother you so much that it becomes difficult to use the phone at that time. This pop will recommend you itself to install the new app.
2) Demand for money
Some hackers are so dangerous that they completely take over your phone and demand money from you. They do not ask for cash from you, they demand in such a way that they force you to make online payment or purchase. Not only this, many times the balance of your phone flies without informing you or the bill starts increasing.
As we have already told in above points about extorting money in form of digital currencies.
3) Phone behavior will change
One symptom of a smartphone being hacked is that it starts to act strange. You will close the phone and it will start opening the application by itself. Not only this, the data of your phone will also increase significantly.
4) Spam downloading
One symptom of being hacked is that your phone will start downloading apps by itself. Even if you try to stop that download, it will not stop. Even if it stops then the downloading starts by itself. At the same time, there are more complaints of phone heating after hacking.
We recommend these top 4 antivirus
For PC, Android and IOS user
Nortorn 360 DeluxAvast
Sophos Intercept X
Panda Dome premium 2020
We are telling you one of the best application for you phones and how to secure it. So please go and read our previous blog How To Secure Your SmartPhone?
Hope you enjoyed this. Keep connected.
Take Care
Stay Home Stay Safe
HASTA LA VISTA



it is the great stuff keep going on
ReplyDeletethanks and keep support
Deletehii this side jack from U.K please upload the video
ReplyDeletesure very soon our team will upload a video
DeleteHii i am sunil singh from india please make on your previous topic.
ReplyDeletehow to hack a android. and share it please. it's difficult to understand by this because i am facing lot's of problem when i do this practical please upload video.
sure brother we will upload a video on this topic very soon.
Deletebhai mera system hack ho gaya hai toh kya karu. batao yaar please.
ReplyDeletebrother humari team ne issme hi solution bataya hai. dhyan se dekho aur agr phir bhi naa ho toh comment mai mention karo.
Delete